Phishing is a type of online scam where criminals impersonate legitimate organizations via email, text message, advertisement or other means in order to steal sensitive information. Email has been the major platform to deliver and Execute a Phishing attack. And cyber analysts have been dedicating their time to analyzing Emails validating the malicious Email from the real one. It has been a real waste of time dealing with such problem and in order to solve this problem there are Automation tools that really helps analysts on analyzing Emails Like ThePhish

ThePhish: Learn about an Automated Phishing Email Analysis Tool
Also Read: Zphisher - Automated Phishing Tool for Social Media Accounts Hacking
ThePhish is an automated tool for analyzing an Email whether it is malicious or valid. This tool is a web application that is based on three open source tools called TheHive, Cortex and Misp. One of the major features is the tool enables the analyst to interfere in the analysis process and help with the analysis process. This tool uses Python API TheHive4py and Contex4py to Communicate.
TheHive : is a Popular open source Security incident Response platform. This tool has a specialized tool like alert feeders that are built to consume a security event like phishing, parse it and create an alert in TheHive. This tool contains an observable like Ip addresses, Email addresses, URLs, domains
Cortex : It is a powerful web based observable analysis and active response tool. They have two types of tasks. The usage of Cortex is based on neurons, which are autonomous applications managed by and run through the Cortex core engine.
- Analyzers : they analyze different types of observables and interaction with the services that speed up the process of analyzing. The analyzer have many tools embedded in it such as VirusTotal, io, urlscan.io, AbuseIPDB and PhishTank.
- Responder : only useful when cortex is working with TheHive
MISP(Malware Information Sharing Platform): This tool helps sharing information about Threat intelligence. The tools help how to best countermeasure against targeted attack. They not only send but also receive from trusted partners. The basic building block of MISP is the event. Each event is made up of a list of attributes, which are atomic pieces of data that could be IoCs. It Is also a web based tool that makes sharing threat info easy for effective detection of attack.
Cortex and MISP(Malware Information Sharing Platform) will be integrated with TheHive to allow us to analyze observables such as IP address, files, hashes and etc against a wealth of security information through various community driven feeds. That can enable cyber Security Professionals with rapid accessibility of information to respond to any potential incident at hand as quickly as possible.
How do they work together ?
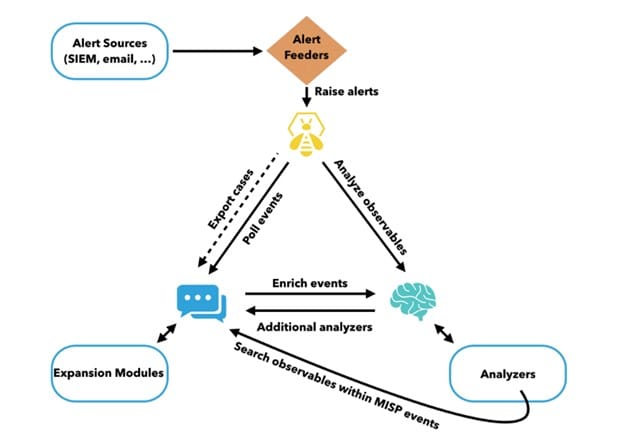
The First thing is Events like Email will be consumed by Alert Feeders. These Alert Feeders will alert TheHive using the API provided called TheHive4py.
The analyst can create a case from Cortex and analyze observables and also interact with MISP through Cortex with a special tool called MISP Search Analyzer. This analyzer makes it possible to search observables within a MISP instance. The observables can also be analyzed with the invocation of MISP expansion modules. Moreover, it is possible to launch responders to automate certain actions, like sending a notification email.
The illustrated figure shows the entire procedure on how those 3 tools work together.
How does ThePhish work ?
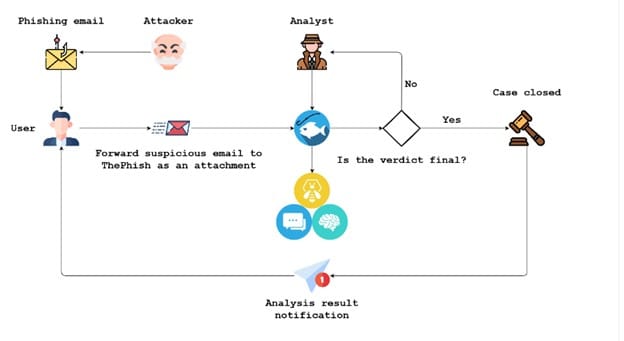
After the attacker crafts a phishing Email and sends the malicious Email to the User, The user will send the Email with the EML format to the MailBox used by ThePhish. After the Analyst selects Email to be analyzed.
The next task will be ThePhish extracts Observables from the Email and creates a case on TheHive which will be analyzed by Cortex’s Analyzer. Then ThePhish will decide about the content of Email whether it is malicious or not or will need further investigation. If the Email is malicious ThePhish will export the case to MISP and if it needs further investigation the analyst will intervene on the analysis process and notify the user.
Installation and Configuration
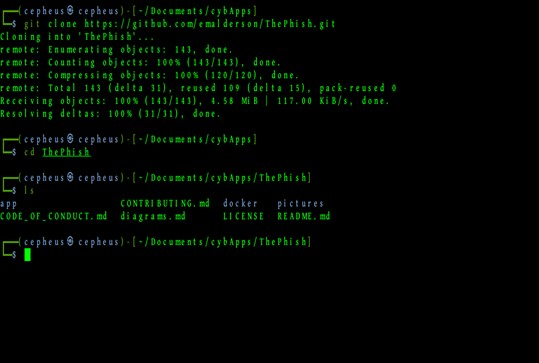
We have many ways to install ThePhish but for now we will install it with docker-compose. The first step is going to be cloning the repository from github https://github.com/emalderson/ThePhish.git and go to the directory docker with the command cd docker as shown below.
NOTE:
>>> git clone https://github.com/emalderson/ThePhish.git
>>> cd docker
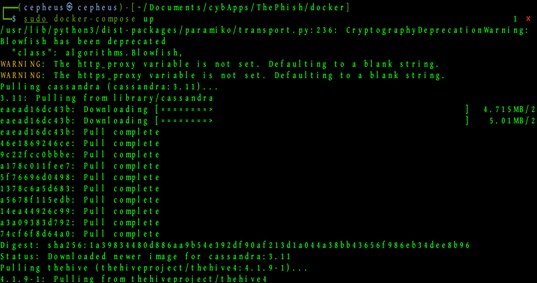
The next step is going to be pulling from the docker container with the below command.
>>> sudo docker-compose up
Usage
The first step is for the users to send a suspicious looking Email for the Mailbox of ThePhish with the EML format to avoid running into errors to analyze phishing email.
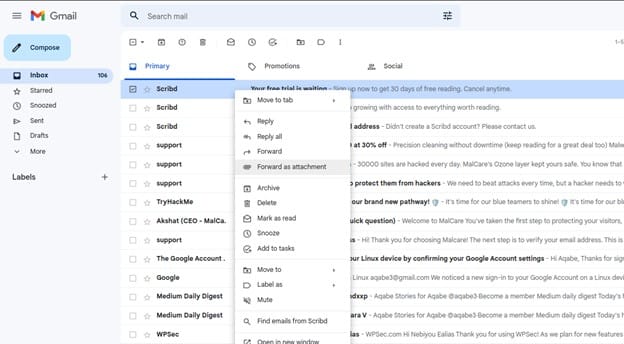
Then the analyst receives the suspicious Email and selects it for investigation as the below picture shows and start the analysis process in the ThePhish Panel.
As the Analysis Process begins we can see the progress log as shown below.
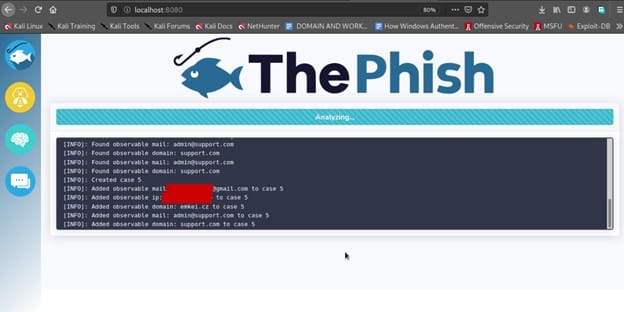
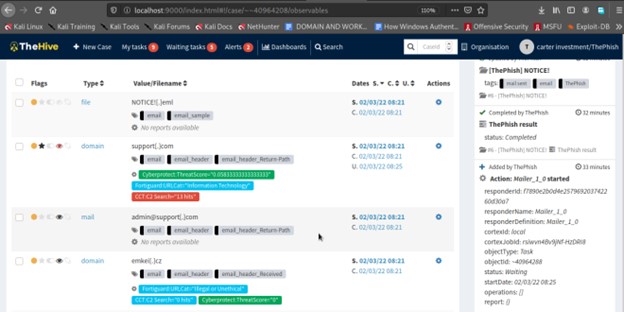
While in the background the ThePhish starts to create a case on TheHive and all the observable features important for the analysis i.e domains, attachments and IP addresses are extracted.
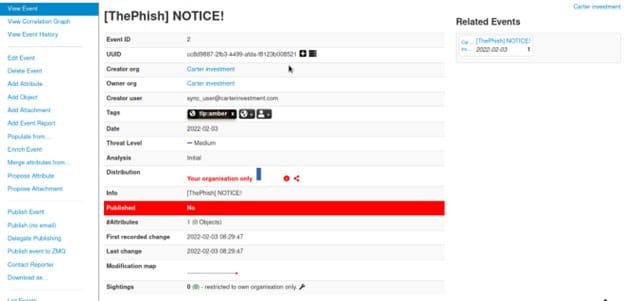
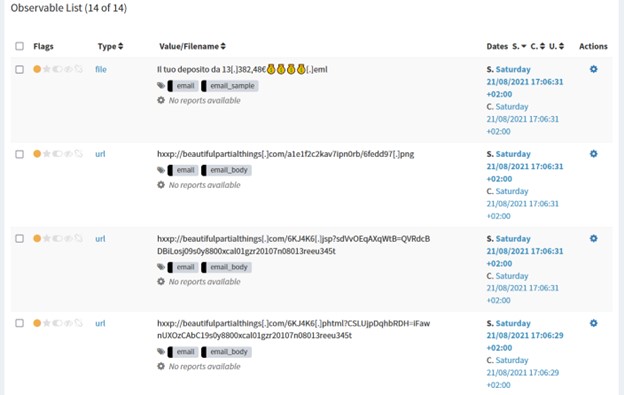
Each of the observables extracted represent the case which is exported as an event in MISP as shown on the image below.
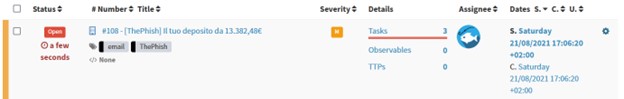
After the extraction of those features all the observable features are added to the case.
Since the analysis process takes place on theHive too we can see the progress while it is being analyzed.
Then after finishing the analysis process ThePhish will decide whether the Email sent from the user is malicious or not. If the Email is malicious the platform will tag all the observable in the Email as IOC(Indicator Of Compromise).
Next ThePhish will stop the case after analyzing and classifying the imported Email.
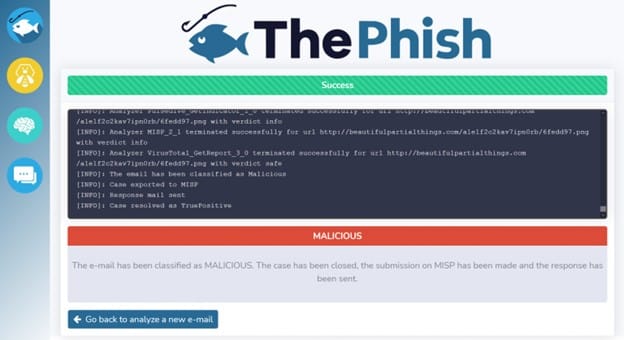
The Final step will be to inform the user whether the Email forwarded was malicious or not using an Email.
Conclusion
In This article we have seen how a malicious Email can be detected and automate the process of classifying it into malicious and valid Email using the tool ThePhish. It is a web application written in Python 3 and based on Flask that automates the entire analysis process starting from the extraction of the observables from the header and the body of an email to the elaboration of a verdict which is final in most cases.
ThePhish uses other open source yet powerful tools (MISP, Cortex and TheHive). This tool makes it easier even for the user who forwards a suspicious email for analysis to ThePhish. It requires the analyst’s intervention when necessary, but with the most tedious and mechanical tasks already performed.